Big Tech Does Not Secure Your Phone Number & Your Emails Can Be Hacked & Bitcoin Stolen
Hackers Have Stolen Millions Of Dollars In Bitcoin — Using Only Phone Numbers
Laura ShinFormer ContributorCrypto & BlockchainI write and podcast about crypto/blockchain technology.This article is more than 4 years old.
Just after midnight on August 11, self-professed night owl Jered Kenna was working at home in Medellin, Colombia, when he was notified the passwords had been reset on two of his email addresses.
He tried to set up new passwords himself by prompting the email service to send him text messages containing a code — but they never arrived.
“So I called the company to make sure I hadn’t forgotten to pay my phone bill, and they said, you don’t have a phone with us. You transferred your phone away to another company,” he says. A hacker had faked his identity and transferred his phone number from T-Mobile to a carrier called Bandwidth that was linked to a Google Voice account in the hacker’s possession. Once all the calls and messages to Kenna’s number were being routed to them, the hacker(s) then reset the passwords for Kenna’s email addresses by having the SMS codes sent to them (or, technically, to Kenna’s number, newly in their possession). Within seven minutes of being locked out of his first account, Kenna was shut out of of up to 30 others, including two banks, PayPal, two bitcoin services — and, crucially, his Windows account, which was the key to his PC.
While this would wreak havoc on anyone’s life, it had especially disastrous consequences for Kenna. “I’m an early bitcoiner,” he says. “I don’t think you have to say anything else.”
Kenna was so early in bitcoin that he remembers when he would plug his computer into the network and see only four other computers running it. Now, there are more than 5,000. Computers supporting the network are slated into a competition to win bitcoin roughly every 10 minutes. In the early days, the payout was 50 bitcoin each time; now it’s 12.5. Kenna recalls that at a certain point, when he was “only” winning 50 bitcoins a day, he stopped supporting the network, thinking it wasn’t worth it. At today’s price, he was giving up on $40,000 a day.
Though he did have some bitcoins in online services, particularly since his businesses accept bitcoin as payment, he kept almost all his bitcoins on an encrypted hard drive. “It was essentially my never-sell-this-until-it-goes-to-a-billion-dollars nest egg,” he says. He had kept it offline for most of the past several years, but had connected that device in recent weeks to move them somewhere more secure and sell some. Though he had locked it with a 30-character password, the hackers moved the coins off. And unlike a credit card transaction, a transfer of a cryptocurrency is irreversible.
When asked how many bitcoins he lost, Kenna laughs. Confirming only that it was millions of dollars’ worth, he says, “I was one of the first people to actually do anything in bitcoin and I no longer have any bitcoin to speak of,” he says. “I’ve got, like, 60 coins or something, which is nothing compared to — it’s a fraction.”
PROMOTED
Plus, he still does not have his number back. (T-Mobile declined to discuss individual customer cases.)
In a larger wave of bitcoin scams that have hit everyone from everyday people to hospitals, Kenna’s experience is only one of a spate of recent hackings of high-profile cryptocurrency industry players such as venture capitalists, entrepreneurs, C-level executives and others who have had their phone numbers hijacked, some of whom have also suffered financial losses, several of whom have been threatened or ransomed, and one of whom was put in physical danger.
Their experience is part of a larger trend. In January 2013, the Federal Trade Commission received 1,038 reports of these incidents, representing 3.2% of all identity theft reports to the FTC that month. By January 2016, 2,658 such incidents were filed — 6.3% of all such reports that month. There have been incidents involving all four of the major carriers.
While it’s difficult to put a number on the cryptocurrency hackings, Coinbase, the highest-volume U.S.-based cryptocurrency exchange, says it is on track to see double the number of such cases from November to December among its customers. Industry-wide, targets have included venture capitalists Adam Draper, Brock Pierce, Bo Shen and Steve Waterhouse, an unnamed executive at Coinbase, Gem chief executive Micah Winkelspecht, former Bitfury executive Michael Golomb, early Bitcoiner and entrepreneur Charlie Shrem, miner Joby Weeks, developer Joel Dietz, six affiliates of a decentralized prediction platform Augur, a database on the Ethereum forum, and others who declined to be named for fear of being further targeted.
While many of them did not take a financial hit, several did, with Kenna’s losses among the largest. Shen had $300,000 of his Augur REP tokens taken, plus an undisclosed amount of bitcoin and other cryptocurrencies. Weeks lost about $100,000 worth of bitcoin, and was cleaned out of his holdings in lesser known cryptocurrencies such as Ether, Ripple and Monero. Additionally, his friends also collectively gave the hacker, who posed as Weeks requesting to “borrow” money, $50,000 worth of cryptocurrency. (Weeks has introduced many people to bitcoin over the years by giving away what he claims is about 1,000 bitcoins, so his friends are well-versed in sending digital currency to each other.) Kenna and other victims also said their hackers have been hitting up friends for bitcoin and other virtual currencies.
But the security weakness being exploited here is not one that only affects cryptocurrency industry players — they are simply being targeted first because such transactions cannot be undone. The security loophole these hackers are milking can be used against anyone who uses their phone number for security for services as common as Google, iCloud, a plethora of banks, PayPal, Dropbox, Evernote, Facebook, Twitter, and many others. The hackers have infiltrated bank accounts and tried to initiate wire transfers; used credit cards to rack up charges; gotten into Dropbox accounts containing copies of passports, credit cards and tax returns; and extorted victims using incriminating information found in their email accounts.
Blockchain Capital VC Pierce, whose number was hijacked last Tuesday, says he told his T-Mobile customer service representative, “It’s going to go from five customers to 500. It’s going to become an epidemic, and you need to think of me as the canary in the coal mine.”

Shutterstock
The Phone As Your Identity
In all these cases, as with Kenna’s, the hackers don’t even need specialized computer knowledge. The phone number is the key. And the way to it get control of it is to find a security-lax customer service representative at a telecom carrier. Then the hacker can use the common security measure called two-factor authentication (2FA) via text. Logging in with 2FA via SMS is supposed to add an extra layer of security beyond your password by requiring you to input a code you receive via SMS (or sometimes phone call) on your mobile phone. All fine and dandy if you’re in possession of your phone number. But if it’s been forwarded or ported to your hacker’s device, then that code is sent straight to them, giving them the keys to your email, bank accounts, cryptocurrency, Facebook and Twitter accounts, and more.
Last summer, the National Institutes of Standards and Technology, which sets security standards for the federal government, “deprecated” or indicated it would likely remove support for 2FA via SMS for security. While the security level for the private sector is different from that of the government, Paul Grassi, NIST senior standards and technology advisor, says SMS “never really proved possession of a phone because you can forward your text messages or get them on email or on your Verizon website with just a password. It really wasn’t proving that second factor.”
Worst of all is if the hacker doesn’t have your password but the password recovery process is done via SMS. Then they can reset your password with just your phone number — one factor.
But 2FA via SMS is ubiquitous because of its ease of use. “Not everyone is running around with a smartphone. Some people still have dumb phones,” says Android security researcher Jon Sawyer. “If Google cut off 2FA via SMS, then everybody with a dumb phone would have no two-factor at all. So what’s worse — no two-factor or two-factor that is getting hacked?” (At the end of 2016, 2.56 billion non-smartphones and 3.6 billion smartphones will be in use worldwide, according to mobile industry market research firm CCS Insight.)
This is exactly why Google says it offers 2FA via SMS — it is the method that could offer the most users an extra layer of security. The company also offers users options with higher levels of security, such as an app called Google Authenticator that randomly generates codes or hardware devices like Yubikeys, for users at higher risk (though one could argue those methods should be used by all users who manage any sensitive information such as bank accounts with their email address).
Even cryptocurrency companies that would seem to fall in that higher risk category still use 2FA via SMS. When asked why Coinbase, which has a reputation for good security, still allows for 2FA via SMS (although it does offer more secure options as well) , director of security Philip Martin responded via email, “Coinbase has about five million users in 32 countries, including the developing world. The unfortunate fact is many users have no better technical alternative than SMS, because they lack a smart phone or the technical confidence and knowledge to use more sophisticated techniques. Given those restrictions, our attitude is any 2FA is better than no 2FA.” Another Bitcoin startup also known for strong security and that also has a growing customer base in emerging markets, Xapo, uses 2FA via SMS but plans to phase it out soon. (Both services have other security measures in place that have prevented users whose phones were hijacked from losing coins.)
Jesse Powell, CEO of U.S.-based exchange Kraken, who wrote an extensive blog post detailing how to secure one’s phone number, blames the telcos for not safekeeping phone numbers even though they are a linchpin in security for so many services, including email. “The [telecom] companies don’t treat your phone number like a bank account, but it should be treated like your bank. If you show up without your pin code or your ID, then they shouldn’t help you,” he says. “But they prioritize convenience above all else.”
He says that attitude especially puts people who own cryptocurrency at risk. “The Bitcoin people have a different threat level,” says Powell. The average person might have photos or private information compromised, or be able to ask their bank to reverse the credit card transaction. “But for people in the bitcoin space, there are real consequences,” he says. “The phone companies aren’t building a service for people who are in charge of millions of dollars. They’re in the business of providing a consumer product.”
Fenbushi Capital’s Shen described a mismatch between the security required so far online versus the kind of security needed for those working at the frontier of cryptocurrency. “I think most of the current services like Google, Yahoo or Facebook or Amazon are working out solutions good for the information web,” he says. “Now we are at the value web, which is real money involved.”
The Hacker’s Weapon Of Choice: “Social Engineering”
In order to find that opening through the customer service representative, hackers often employ what’s called social engineering, used in 66% of all attacks by hackers. An elaborate version is demonstrated in this video (starting around 1:55), in which a woman with a baby crying in the background (really just a YouTube recording) claims she’s newly married and doesn’t know what email address is used to log into her husband’s account. She then has the rep change the email and password, locking the victim out.
“When people think of hackers, they think of someone breaking into your computer through software and that is definitely not the way it is happening nowadays,” says Chris Hadnagy, chief human hacker at Social-Engineer, a firm that educates companies on combating social engineering attacks.
Hadnagy says that with LinkedIn, Facebook, Twitter and FourSquare, “I can create a very accurate psychological profile — what you eat, what music you listen to, your work history, marriage history, I know enough about you to pretext as you with most of your utilities and services.” Birthdates are easily discovered on sites like Facebook and birth years deduced from LinkedIn, so a hacker employing social engineering can use that information to call up, say, a telco and claim they forgot the pin to the account but give a birthdate, phone number and address or even the last four of the Social Security Number since it is so commonly used to identify people, to reset that passcode, Hadnagy says. He also notes that in the last two years, hackers have increasingly been using phones to perpetrate a hack because the ability to “spoof” a line — make it seem like you are calling from another number — has become so easy.
“You can do it through most VoIPs for free, and there’s no way to validate it,” he says. “I can take this number you’re calling me from and call you back in a minute from this number. If this is your cell number and you didn’t have a pin, I can call this number from your number and log right into your voicemail. I can call you from the White House. I can spoof any number in the world.”
In the phone hijacking of Micah Winkelspecht, chief executive and founder of blockchain company Gem, a persistent hacker called T-Mobile six times in one day trying to impersonate him. Five times, the hacker was denied access to the account, but the sixth representative let him in and allowed him to move the line to another phone. “This is not the fault of the customers. It’s the fault of the carriers for not following their authentication procedure,” he says. “I was using a password manager, random passwords, 2FA — you name it, I use it.” Winkelspecht, who didn’t lose any money, says he could take every precautionary method available to him and still be victim because “a single employee at a call center can make a mistake and it can compromise your entire digital identity.”
The experience of Steve Waterhouse, former partner at blockchain and cryptocurrency venture capital firm Pantera Capital, shows just how easy it could be to social engineer when dealing with a customer service agent eager to help. Hijackers ported his number to carrier Bandwidth two months ago. When he recently got his number back, he called up Verizon to turn on international dialing again. The customer service representative asked for the pin on his account. “I said, hang on, let me just remember, because I have a series of businesses and different accounts, and the guy’s like, oh, don’t worry about it, just give me the last four of your Social. I said, whoa, what’s the point of the password then? And he was like, well, you know. And I said, Can I port my number? Actually, I didn’t want to port it — it was a test. And he was like, yeah, no problem, where do you want to send it? And I said, I thought I had port blocking turned on, and he said, hang on, let me look at my notes. And there isn’t a field for this, it’s buried in a series of notes from different customer reps. And he said, oh, that’s right, this happened to you before. Oh wow, you have a high security level. Oh shoot, someone should have put that up at the top of the note. I said, Oh great, so it’s just random. If I get the right person, I can port my number then, and he was like, no, of course not. I thought, this doesn’t sound like security to me.” (Verizon declined to discuss the cases of any individual customers.)
The hackers have a multitude of avenues to obtain personal information. Waterhouse’s hacker initially texted him pretending to be a friend and claimed he was writing a blog post about Waterhouse and his wife and needed to know where they met — information necessary to answer a security question. The hacker of the Coinbase executive tried messaging other execs to change his email password. One hacker told his target that he called up an online retailer up, pretended to be him and said he wasn’t sure what address and number he had on file in order to obtain those pieces of information, which he then used with the telco. (Totally plausible but not true in this case: the retailer hasn’t had any contact with anyone claiming to be this customer for more than a year.)
A number of hackers have gone after the true target’s loved ones either to get access to their phone number or just to hijack the loved one’s account and then extort the target. For instance, Pierce had taken the extra security measure of not having his phone in his name but in the name of a woman with whom he has a personal relationship. On December 9, a man pretending to be Pierce called T-Mobile, requesting her account number. She had a password on the account that the caller is required to give before anyone can gain access to the account, but she says T-Mobile told her the representative forgot to take this step. On the 13th, someone impersonating Pierce called T-Mobile, gave the account holder’s name and the last four of her Social Security Number and ported Pierce’s number to Sprint.
The hacker went after the phone number of Shrem’s fiance. Last July, while he was on the phone with her, she said she noticed her Gmail account wasn’t working, and then within minutes, her phone went dead. Shrem tried to log into her laptop, a Mac, but it said that the device had been reported stolen and had been wiped — the hacker had likely reset her iCloud password via SMS code and then reported it stolen and had it remotely wiped. The hacker then texted Shrem, posing as her, asking for 50 bitcoins.

The text message Shrem’s hacker sent him, posing as Shrem’s girlfriend. (Courtesy of Charlie Shrem)
Regulations Leave Security Up To Carriers
In the early 2000s, the Federal Communications Commission implemented rules requiring carriers to port when they receive a valid request, to prevent them from holding customers hostage to their service. To initiate a port, the new carrier must obtain the telephone number, account number, zip code and passcode — if the customer has chosen to use one.
As for verifying and protecting identity, “Carriers have a duty under the law to protect customer information, and the FCC’s recent privacy order strengthened customer data security rules,” FCC spokesperson Mark Wigfield said in an emailed statement. Though the rules were reported as being for broadband companies, they also apply to cellular operators although are not targeted specifically at preventing phone hijackings. The FCC offers guidelines on how carriers should protect customer information, such as “implementing up-to-date and relevant industry best practices” and “robust customer authentication tools,” but the exact process is up to each company.
Sprint, Verizon and T-Mobile declined to comment for this story, as did the Number Portability Administration Carrier, which manages the system that enables number portability. John Marinho, vice president of technology and cybersecurity at cellular industry organization CTIA, released a statement via email, “All of our members consider the privacy and security of their customers to be their highest priority. They each have extensive procedures and protocols in place to protect the personal information and data of their customers and respond to the evolving security landscape.”
FCC rules do not require carriers to offer “port freezes,” and it does not appear that attempts to do so have any effect. Both Waterhouse and Weeks told their providers (Verizon and T-Mobile, respectively) to notate on the account that they were being targeted for hacks and not to port the numbers. That did nothing to prevent the hijackings. (A number managed by Google Voice, however, can be locked, preventing it from being ported.)
Who Are The Hackers?
Several people have communicated with their hackers, even by phone. While many of the IP addresses lead to the Philippines, most of those who spoke to their hackers by phone said their hackers sounded like 20-something American men; one said his was Filipino. Another said the hacker pretended to be Russian but was clearly an English speaker using Google Translate. (He had messaged a native Russian speaker.) But most victims agree that it isn’t a lone hacker, but a team or multiple teams — which is likely how they are able to breach so many accounts in such a short time period once they do hijack a number.
Once they’ve breached an account, the hackers seem to comb that victim’s data for other contacts. Golomb, the former Bitfury executive, said that once the hackers were in his Dropbox, he was able to see that someone in the Philippines was doing searches in his files for words like “bitcoin,” “wallets,” and the names of Bitfury executives and board members, particularly those who might have had the login credentials to the company’s bank accounts. Some victims said their hacker told them he targeted people involved in Ethereum, the second most popular cryptocurrency network to Bitcoin. The FBI is investigating the crimes but declined to comment.
Though Kenna has his theories on who the hackers are, all he would say is, “It’s incredibly sophisticated and incredibly organized. These are the kind of people who, if they were on the other side, I would hire in a heartbeat. They’re incredibly good at being criminals.”
And as for his financial loss, he says, “Obviously it didn’t feel good, but it was kind of relieving. For the first time in the last six years, I feel like no one can steal my bitcoins.” He laughs softly. “In the past, I had people threatening my family, people would send me pictures of my mother’s house, demanding bitcoins and stuff like that. So to be honest, the amount of attempts I’ve had to steal everything — threats on people I care about and hacking attempts and DDOS attacks and blackmail and hacking people to get to me — the fact that it’s over kind of feels like there’s some closure. But that sure as hell doesn’t mean I’m happy about it.”
Read the related story: Hackers Are Hijacking Phone Numbers And Breaking Into Email, Bank Accounts: How To Protect Yourself.
Update, 3:45pm EST, December 20, 2016: This post has been updated to state that Coinbase offers more secure options than 2FA via SMS and that there have been Coinbase and Xapo customers whose phones were hijacked who did not lose coins because these companies have additional security measures aside from 2FA via SMS in place.
7:45pm EST: This post has been updated to add that an Ethereum forum was hacked in the same manner.Follow me on LinkedIn. Check out my website. Laura Shin
Security Advisory: Mobile Phones
- BY KRAKENFX
- POSTED ON

Heed this or perish.
Let’s begin with the assumption that within 24 hours your usual mobile phone number will be hijacked by social engineers. They will use your number to gain access to every account you own that utilizes phone-based authentication and account recovery, like your email. They will then use that access and information to compromise more accounts, and harass, steal, blackmail and extort you and your associates.
In the past month, there’ve been at least 10 cases of people publicly involved in the cryptocurrency scene being victimized by mobile phone hijacking. The consequences have been expensive, embarrassing, enduring, and, in at least one case, life-threatening.
If you are in any way publicly involved in cryptocurrency, consider yourself an active target. You need to immediately audit the security of your accounts – especially email, social media, social networking and mobile phone.
Somehow, the masses have been led to believe that phone numbers are inextricably bound to identities and therefore make good authentication tools. There’s a reason that Kraken has never supported SMS-based authentication: The painful reality is that your telco operates at the security level of a third-rate coat check. Here’s an example interaction:
Hacker: Can I have my jacket?
Telco: Sure, can I have your ticket?
Hacker: I lost it.
Telco: Do you remember the number?
Hacker: Nope, but it’s that one right there.
Telco: Ok cool. Here ya go. Please rate 10/10 on survey ^_^
So, we need to achieve three things:
1. A shift in the way we think about phone numbers
2. The securing of your phone number (to the extent possible)
3. The separation of your phone number from any security functions
1. Changing the way we think about phone numbers
Telcos – Give up the security theater. Start thinking of yourselves more like Brinks and less like Toys “R” Us. Or, just be honest about what you offer: a gamble.
Service Providers – Stop accepting (and requiring) SMS as a method to “recover” or bypass all other security features on an account. You’re custodians of valuable identities and information whether you like it or not. You too need to think of yourselves more like a vault. Until Telcos shape up, you’re perpetuating the misconception that phone numbers are secure.
People – Understand that phone calls and SMS should only be used when you have no alternative, secure mode of communication. Certainly, do not mistake a phone number for an identity. Try to stick to services where you actually own your identity, where your communications are private, and where you can authenticate your interlocutor. See: Signal and BitMessage for a good start.
These problems of ownership in mobile numbers, email accounts, domains and other virtual identities are low hanging fruit for Blockchain entrepreneurs. Some attempts have already been made and more solutions are on the horizon. I’m hopeful that we’ll work this out in the next few years.
2. Securing your mobile phone number and telco account
Call your telco and:
- Set a passcode/PIN on your account
- Make sure it applies to ALL account changes
- Make sure it applies to all numbers on the account
- Ask them what happens if you forget the passcode
- Ask them what happens if you lose that too
- Institute a port freeze
- Institute a SIM lock
- Add a high-risk flag
- Close your online web-based management account
- Block future registration to online management system
- Hack yo’ self
- See what information they will leak
- See what account changes you can make
Secure the email address associated with your telco account
- Create a new email address that you only use with your telco
- Assume that telco agents will leak this to any caller
- Try something like:
- STOP.DO.NOT.PORT.THIS.NUMBER@kraken.com
- they might think twice before doing something stupid
- SKEET.SKEET.SKEET.SKEET@kraken.com
- they might be prohibited from saying this on the call
- ijljj1IiiOlI0oiiljlIlj1llillOjlli0Ijilolljoij1l0jilI@kraken.com
- they might not be able to accurately read it back to the attacker
- STOP.DO.NOT.PORT.THIS.NUMBER@kraken.com
- Make sure the email account is extremely secure
- Passcode bypass instructions will go to this email account
- Instructions on securing email, below
Consider switching to a more secure telco, without a human interface
- Google Fi
- No phone support agents
- No physical locations
- No problems
- No known, comparable other options
Consider setting up a proxy phone number to hide your real one
- Google Voice
- Port your old main number to Google Voice
- Get a new number with Telco and never use it for anything but GV
- Handle all calls through Google Voice
- No known, comparable other options
Pray
- Sacrifice your virgins now because, ultimately, Xenu’s graces are the only thing preventing your phone number from being ported to a 12-year-old in Syria
- There is no 100% sure way to prevent the theft of your phone number
3. Separating your phone number from security functions
Upgrade to secure 2FA methods wherever possible
- Google Authenticator
- Yubikey
- U2F security key
Use SMS only where absolutely necessary and consider whether you want it at all if it will also be used for account “recovery” or password bypass. Ask yourself what are the chances of your password being stolen vs your mobile phone number being stolen.
If you must use SMS, you have two options:
Option A:
- Get a secret, low tech, pre-paid burner phone
- Pay cash for the device and minutes
- Don’t attach your identity (name, address, birthday) to it
- Don’t attach your credit card to it
- Don’t tell anyone about it
- Use it exclusively for SMS two-factor and account recovery
- Change it if any services you use it with get hacked
Option B (recommended):
- Get a Google Voice (with SMS) number
- Don’t attach your identity (name, address, birthday) to it
- Don’t attach your credit card to it
- Don’t tell anyone about it
- Don’t use the accompanying email address, drive or other services
- Use it exclusively for SMS two-factor and account recovery
- Change it if any services you use it with get hacked
- Set up Google Authenticator or U2F as the only two-factor method
- Disable account recovery
An advantage of Option B is that you can (relatively) securely share access to the SMS messages through SMS-to-email forwarding rules, and by sharing the two-factor method’s seed.
It is recommended that you keep your interactions with this Google Voice number and its SMS messages to a device separate from your primary computer and smartphone. An old smartphone would be a good option.
It is recommended that you keep a copy of your GA seed or U2F key in cold storage, else you should be prepared for the consequences of permanently losing access to the number. Decide for yourself what’s worse: your losing access or an attacker gaining access, and secure yourself accordingly.
What follows are step-by-step instructions for setting up a secure Google account (Gmail, Voice, Drive, YouTube, etc.), and following that, steps for setting up Google Voice.
Step 1: Sign up for a new account at https://voice.google.com
In order to ensure that your account is not recoverable through answering “security” questions, randomize your personal information.

Step 2: edit My Account settings
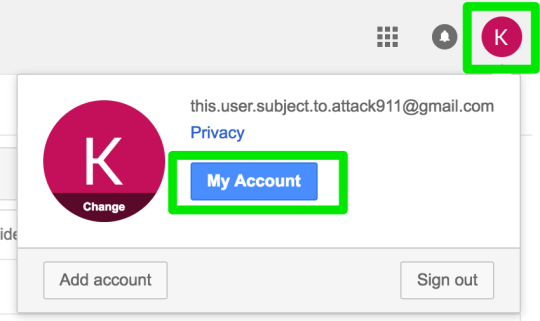
Step 3: Look for ‘Signing in to Google’ on the left
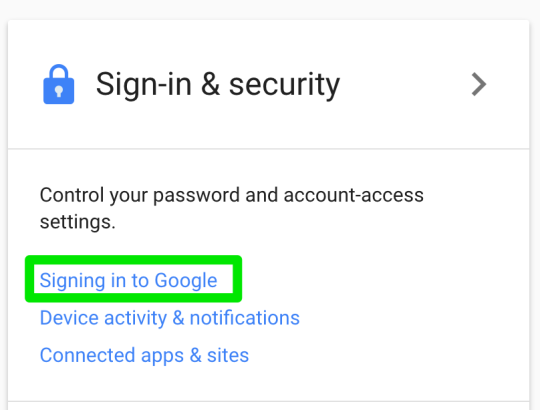
Step 4: enable 2-step verification
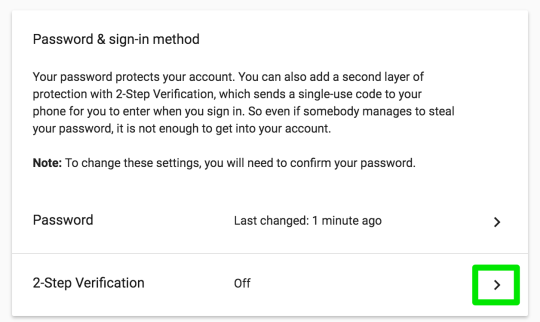
Step 5: you’ll need to first set up SMS 2-step verification before you can add one of the secure methods.
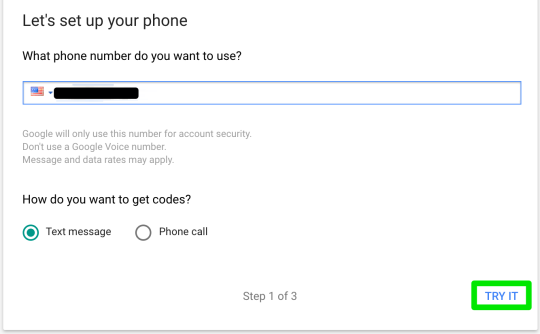
Step 6: enter SMS confirmation code
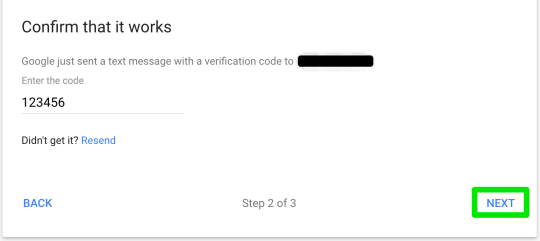
Step 7: turn it on

Step 8 (OPTIONAL): Set up back up codes
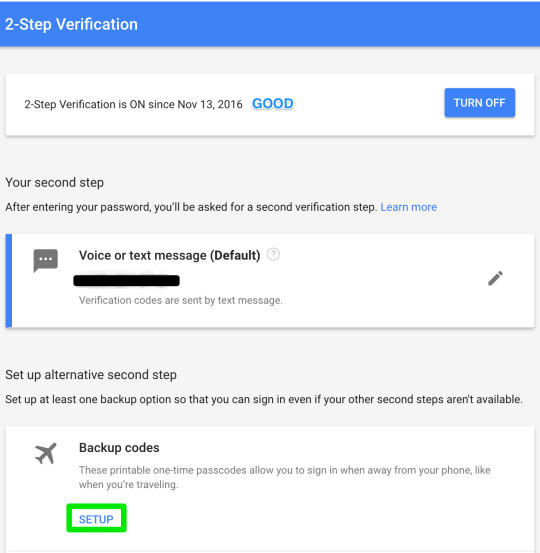
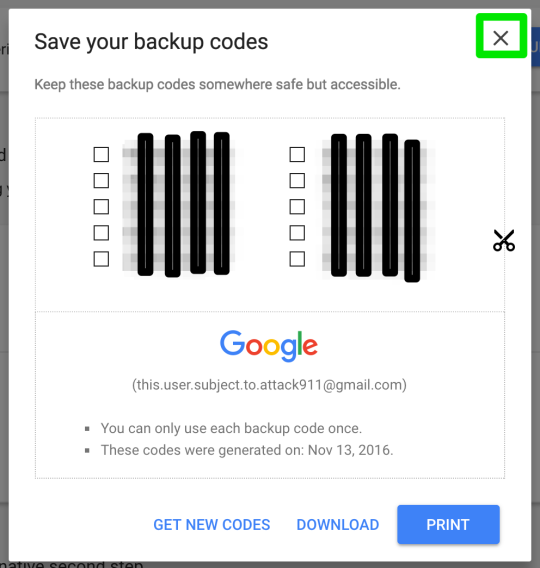
Step 9 (OPTIONAL): save your backup codes in a secure, offline, location.
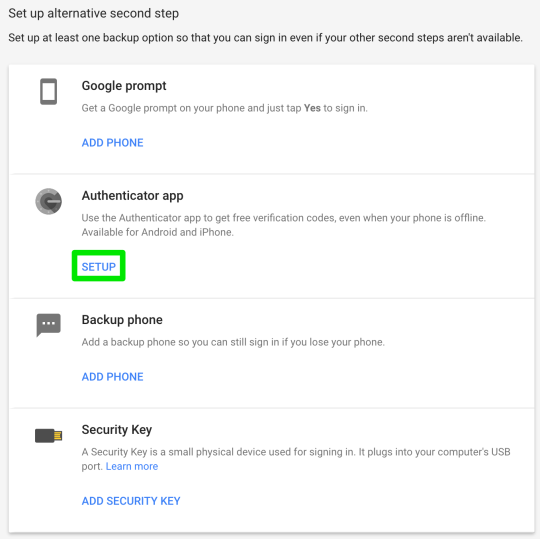
Step 10: set up Google Authenticator (or U2F Security Key)
Step 11: scan QR Code with GA application on secure device
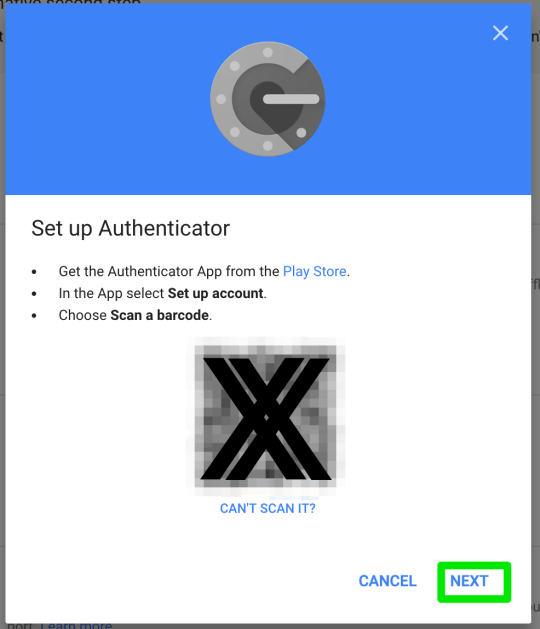
Step 12: enter GA confirmation code shown on GA app
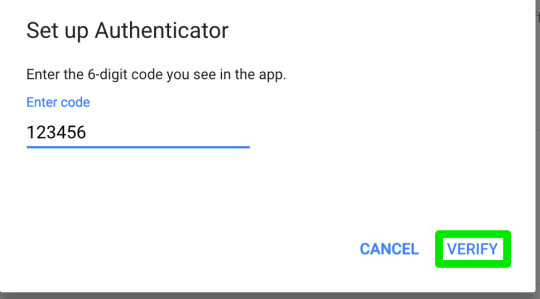
Step 13: click ‘done’ to complete GA setup
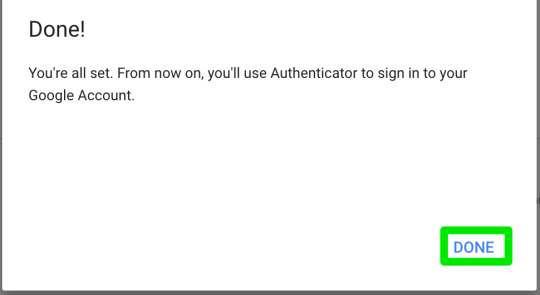
Step 14: remove voice/text as second verification step option
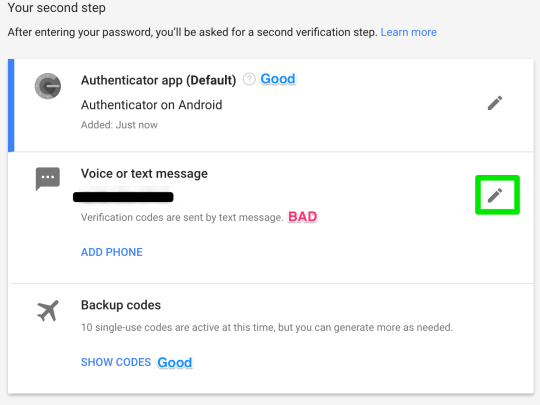
Step 15: confirm phone removal
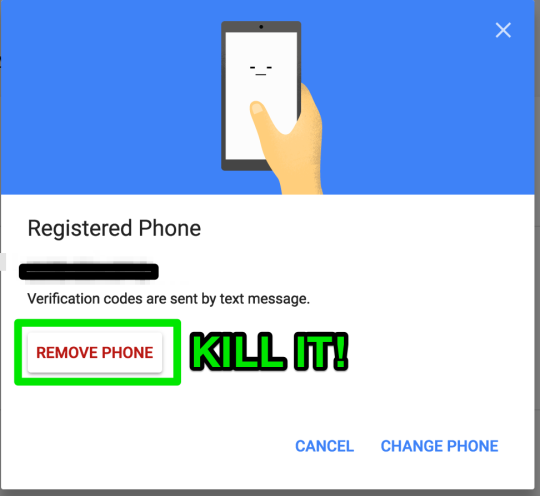
Step 16: confirm phone is removed

Step 17: go back to account settings
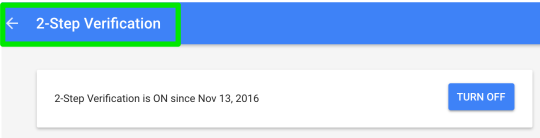
Step 18: under Account recovery options, click email
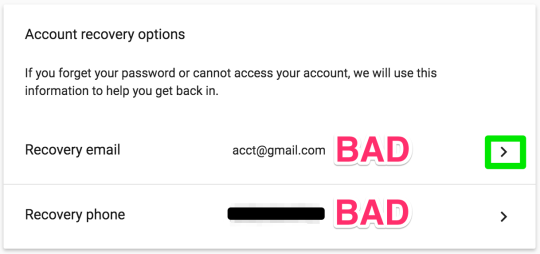
Step 19: delete the recovery email address, leaving the field blank
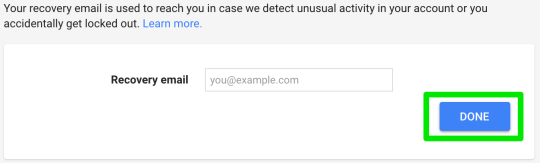
Step 20: delete the recovery phone number
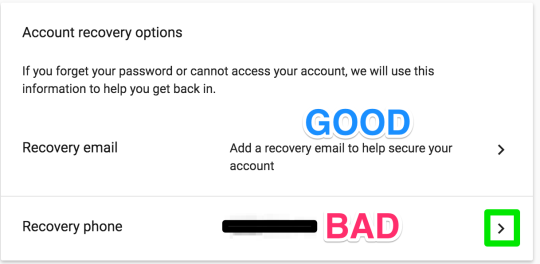
Step 21: edit the recovery phone number
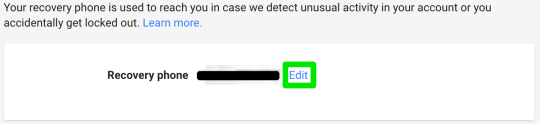
Step 22: remove the recovery phone number
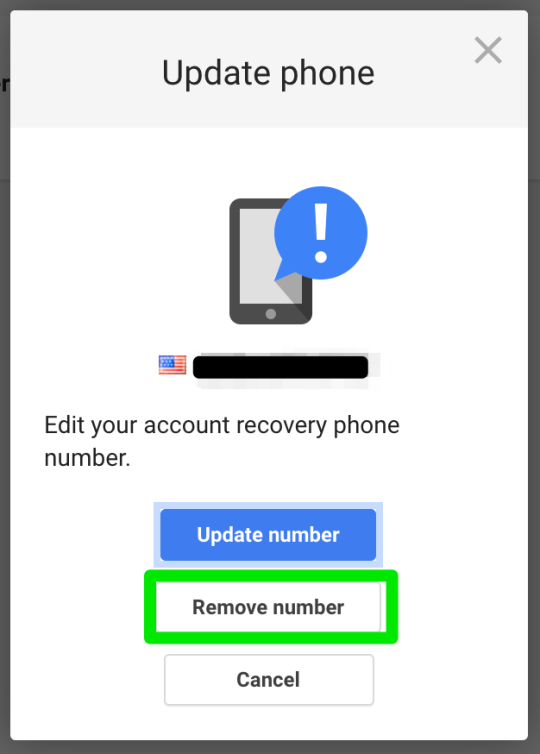
Step 23: confirm removal of recovery phone number
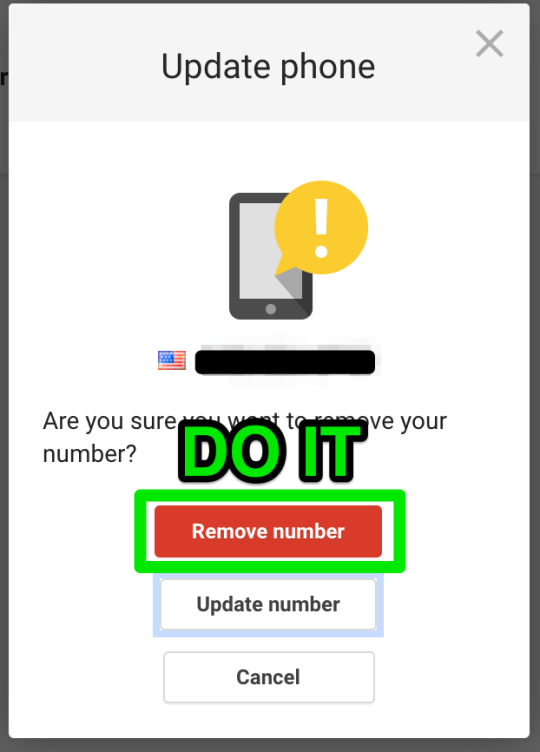
Step 24: confirming that the curse has been lifted
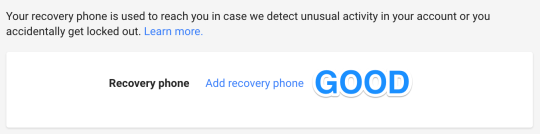
Step 25: go back to sign in settings

Step 26: witness perfection – Google account now secure
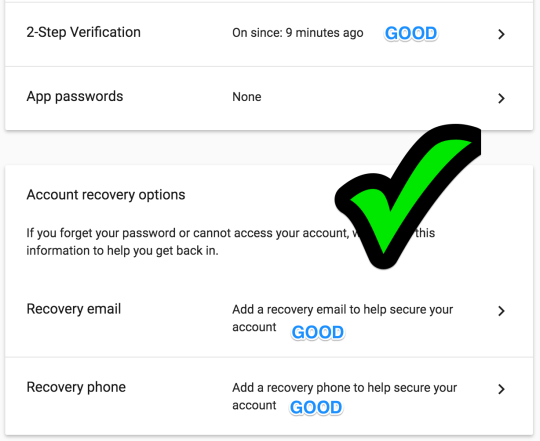
Step 27: on to Google Voice setup

Step 28: get a new number
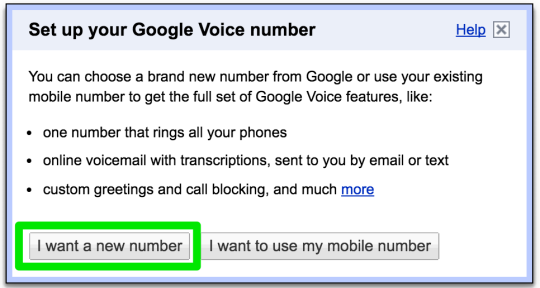
Step 29: add a US forwarding phone (can be removed later)
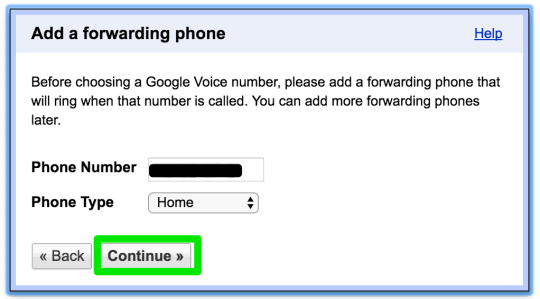
Step 30: verify forwarding phone number
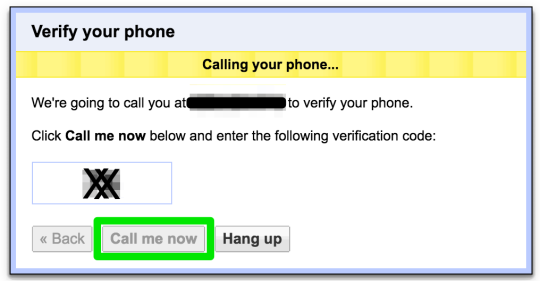
Step 31: search number options
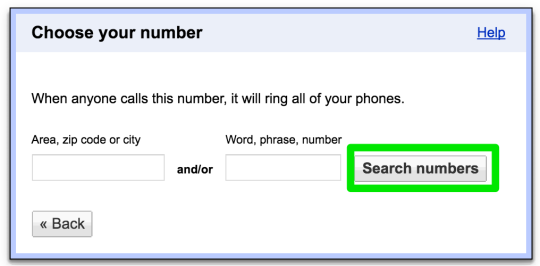
Step 32: select a number
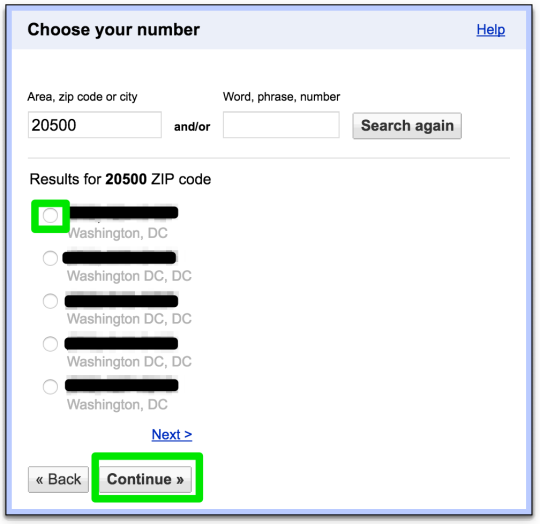
Step 33: finish phone number selection
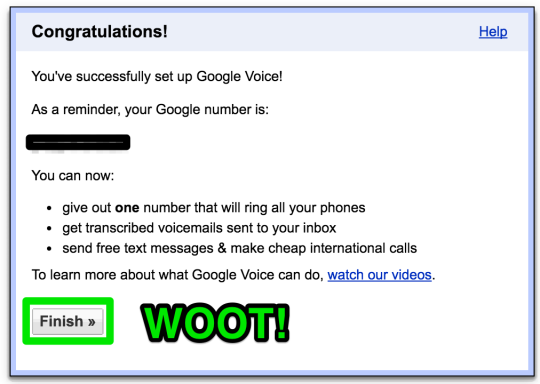
Step 34: remove call forwarding

Step 35: confirm removal of call forwarding
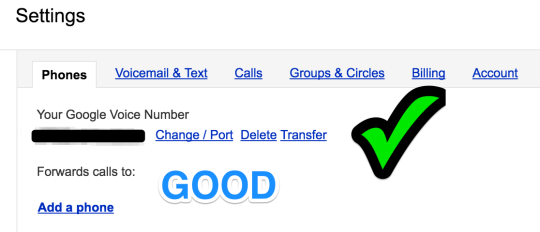
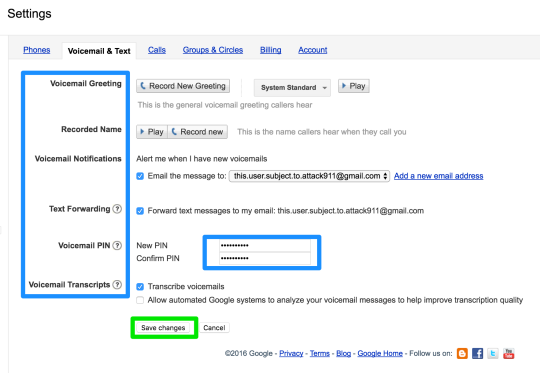
Step 36: configure voicemail & text
Voicemail Greeting: Record blank so as not to reveal any information about the telco or account owner to any random caller
Recorded Name: Record blank
Voicemail Notifications: disable or choose secure recipient, like another secret gmail account that you only use on your 2FA security device
Text Forwarding: disable or choose secure recipient, like another secret gmail account that you only use on your 2FA security device
Voicemail PIN: set at least 8 characters
Voicemail Transcripts: disable
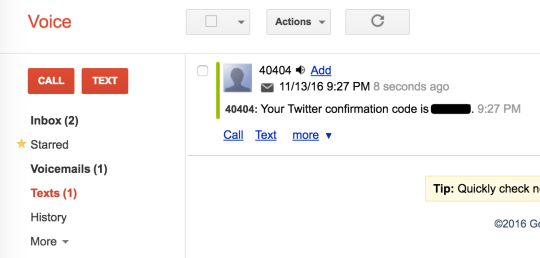
Step 37: test it out
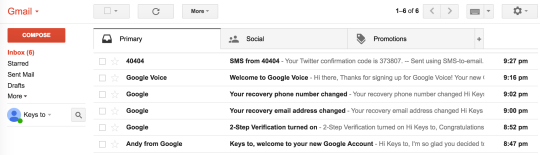
Step 38: review what your email box should look like if you’ve completed all the steps
Step 39: make sure that you never unlock your number
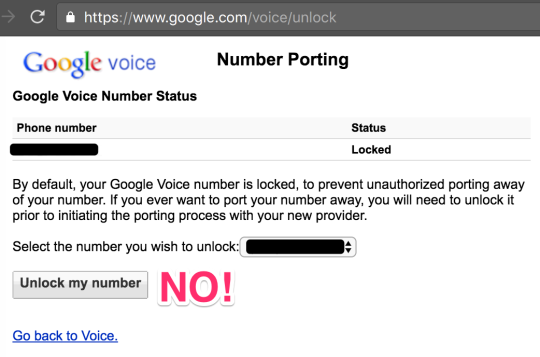
Step 40: relax

More background, resources and reading:
- Coinbase Employee Incident
- FTC Employee Incident
- Popular YouTuber Incident
- Telco Employee Speaks on Security
- Wired: Stop Using SMS 2FA
- NIST Deprecating SMS 2FA
- How Social Engineering is Done
Share this:
Like this:
https://widgets.wp.com/likes/#blog_id=127351137&post_id=219&origin=blog.kraken.com&obj_id=127351137-219-604a1e3af1d50POSTED IN SECURITY, | KRAKEN NEWSTAGGED BITCOIN, BTC, CELL PHONES, MOBILE, MOBILE PHONES, SECURITY, SOCIAL ENGINEERING














